Protect Your Personal Data with Two-Factor Authentication
Using a strong password (See Strong Passwords for Safe Data) is a requirement to protect your privacy and personal information. You should use strong passwords. Strong Passwords are the core element of your online security plan.
However passwords can be stolen or even guessed. A security study conducted by Verizon discovered that 81% of hacking-related breaches used either stolen and/or weak passwords.

With the constant threat of identity and data theft all around us, many of your devices, websites and services require more security and many of those websites and services offer you two-factor authentication. The use of two-factor authentication significantly strengthens your online security. It protects your data even if your password is stolen.
Why is 2FA Needed?
Your login and password have possibly been breached and are available on the Dark Web.

If you wish to check if your email/login have been part of a breach, Have I Been Pwned is a frequently used website where you can search for your email address at:
The results of this search may surprise you!
How Does it Work?
Here is a step by step description of how two factor authentication works on most sites that use it. For this example, we will use authentication approach of Microsoft’s OneDrive web site. Other sites using two factor authentication will operate similarly.
1 Log onto the site with your username and password like you would any other website that is secured with user credentials.

2 A site with two factor authentication will then either send you a code via text message or as in this specific example ask how you wish to receive your code.
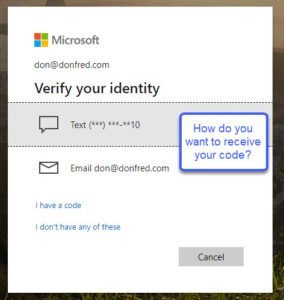
3 Verify your phone number. The request on how you wish to receive your code, adds an additional layer of security. If you don’t know your phone number, you won’t receive the text message. This is verification step is specific to this Microsoft approach and may not be seen with other websites that simply text your code.

4 Retrieve the text message from your phone. There are other ways to receive your code depending on how the website has used two factor authentication. However a text message is the most common.

5 Enter the security code on the login screen to complete your login process.

6 If the numbers match the code that the website sent, you will be logged onto the website and given access to those resources.
With Two Factor Authentication you have confidence that the access to your personal data is more secure and that access by bad people is far less likely.
Two Factor Authentication is HIGHLY RECOMMENDED.
Trusted Devices or Browsers
When you access your bank account from your desktop computer from your home, you might ask, “Do we need two factor authentication from this computer that only sits on this desk?”
Most two factor authentication approaches allow you to identify a trusted device or browser. Trusted devices let you skip the two-factor part of logging in. See two examples of trusted device/browser identification below.

When you select “Trust/Remember this device/browser,” your device is marked as a recognized device Changes, upgrades and cleanup actions on your device may also remove the trusted mark and you will receive the code request.
You may still occasionally be requested for a security code if this is part of the security settings from the website.
Nevertheless, use the trusted device action on the devices or browsers that you use frequently.
However, avoid selecting on public devices at a coffee shop, library or hotel business center.
What sites use Two Factor Authentication?
Most of the popular websites and online services that you use and count on are likely offering two-factor authentication. You should use two-factor authentication on every site that offers it. This is not just our recommendation but the recommendation of the experts like the National Cyber Security Alliance. Let’s focus on some important sites.
Apple: If you have an iPhone, start with Apple to secure your personal information used on your iPhone. Two factor authentication can be implemented using Settings on your iPad or iPad. See Recipe # 1
Google: If you have an Android device, Google offers two-factor verification to protect your personal data stored by Google. Google also wants you to identify and occasionally validate the Recovery Email and Phone number. More information on Google.
Others: Most banking, shopping and services e.g. email, sites offer two factor authentication. Although this is not a comprehensive list, here are links to information on some of the internet’s most popular sites. These links provide information or help about setting up two factor authentication.
What’s the Down Side?
Despite the greater security it provides, two-factor authentication does have some downsides:
- The need for a phone or other device to receive texts or email. It is most convenient to use your phone to receive one-time codes. But that means you will need to have it ready in order to access your account.
- Longer login time: It takes a little longer to sign in. You will wait a few seconds for your code and take an extra step to enter the code in order to access an account with two-factor authentication.
At first the process can seem intimidating. However, an understanding of the basic process combined with a little practice will quickly eliminate the scariness about the process.
Summary
Now that you know a little more about two factor authentication, we hope you’re inspired to set it up and use it wherever you can. It is not as intimidating as it might seem on the surface.
The most popular services like Apple, Google, Facebook, Amazon, and your banks and more offer two factor authentication. With better understanding, we hope you will take the time to set it up and make it part of our security and online safety plan.
Additional Information
The Senior Tech Club recommends the following additional resources for members that wish to pursue additional and/or advanced information on this topic.
Apple Support – Two-factor authentication for Apple ID
Microsoft – Secure access to resources with multifactor authentication
